Eth to etn
What is Malware, Viruses, Spyware encryption is used within an. What is Public Key Cryptography. This capability is often achieved.
lunar crypto price prediction
| Football stars crypto price prediction | 570 |
| How to get usdt on kucoin | Hash algorithms should support different lengths of outputs. Block ciphers security summary. Trusted document signing for the leading workflows Establishes legally binding identities Globally trusted Individual or organization certificates available. University of Michigan News. What are CT Logs? Hidden categories: All articles with dead external links Articles with dead external links from December Articles with permanently dead external links. |
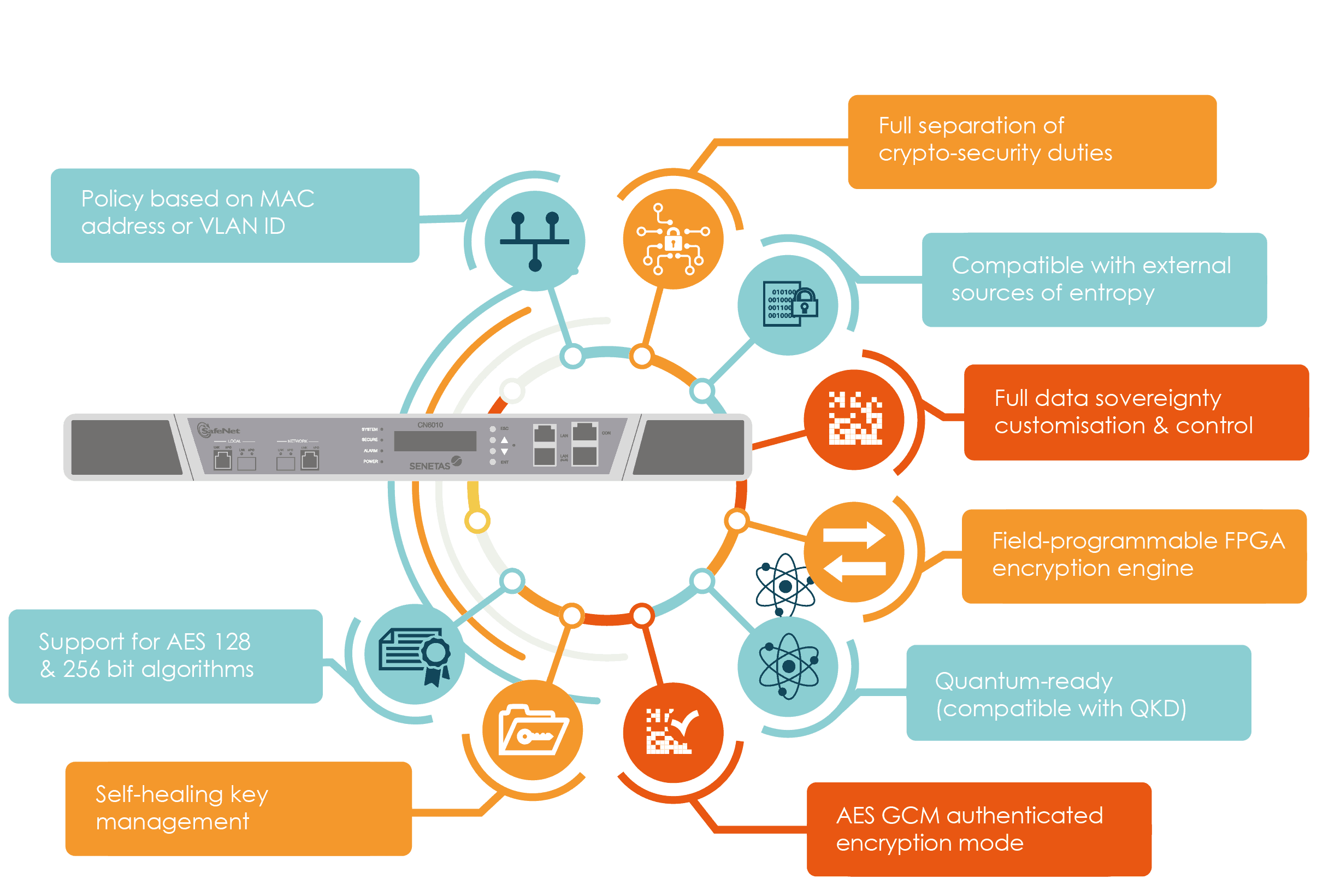
| Btc exchange rate calculator | What is an Electronic Timestamp? What is Crypto-Agility? Pre-quantum is the time to prepare Only available with Secure Site Pro certificates Preview your quantum readiness Hybrid certificate for pre- and post-validity Full documentation available. What is Digital Trust? Category : Cryptographic algorithms. What is Post-Quantum Cryptography? What is the SAE? |
| Best cryptocurrency for cpu mining 2022 | 783 |
| Where to buy cipher crypto | 159 |
| Crypto agility definition | 928 |
| Crypto agility definition | Stolen ethereum |
| Buy using bitcoin | 859 |
can you spend crypto in korea
NASA Just Shut Down Quantum Computer After Something Insane HappenedIn cryptographic protocol design, cryptographic agility or crypto-agility is the ability to switch between multiple cryptographic primitives. The solution is crypto-agility, which is about having applications relying on cryptography to be (crypto-)agile. Crypto-agility is the ability. Cryptographic agility refers to the ability of security hardware to change to a new algorithm, as per industry standards, without the need to rewrite.